
Introduction: Securing Visibility in a Crowded and Competitive World
Are you having trouble reaching CISOs, IT leaders, and decision-makers with your content?
Do your services scream “best-in-class” yet your website receives little to no organic traffic?
In the high-stakes world of cybersecurity, visibility is critical. You may have the most powerful firewall, a groundbreaking zero-trust solution, or the most intelligent AI threat detector—but if no one can discover your company online, it might as well not exist.
That is where Search Engine Optimization (SEO) comes in.
Unlike sponsored advertising, which disappear as your money is depleted, SEO leaves a permanent digital legacy, establishing your company as an authoritative voice in a complicated and competitive field. However, many cybersecurity organizations ignore SEO—often because they consider it “marketing fluff,” or because they feel that technical goods will speak for themselves.
This blog busts that myth wide open.
“Cyber Security SEO: An Expert Guide” is a comprehensive, practical resource designed exclusively for cybersecurity organizations, SaaS suppliers, MSSPs, penetration testers, and cybersecurity consultants. The blog will investigate:
- Why SEO is crucial in the cybersecurity industry
- How to Create a Data-Driven SEO Strategy
- Real-world instances of cybersecurity companies flourishing with SEO.
- On-page, off-page, and technical SEO designed for cyber security subjects
- FAQs about Cyber Security SEO
Let’s get started.
Why Does SEO Matter for Cybersecurity Firms?
SEO is more than simply rankings in an industry that values trust, authority, and technological brilliance. It is also about creating reputation. According to Gartner, the average buyer journey in cybersecurity includes up to 17 content exchanges before engaging with sales.
Trust Starts on Page One.
According to a BrightEdge survey from 2024, 68% of internet encounters start with a search engine, and 75% of people never go beyond the first page. That implies that if your cybersecurity website isn’t optimized, you’ll be almost invisible to the bulk of your intended audience.
Cybersecurity = High Search Volume and High Competition
Whether it’s “zero trust network access (ZTNA),” “managed detection and response (MDR),” or “ransomware prevention tools,” there’s a lot of search volume—but also fierce competition.
Example:
Search term: “Zero Trust Network Access Solutions”
- Monthly searches: around 2,400.
- Keyword Difficulty (Ahrefs): 75/100 (Very hard).
- Top competitors include Palo Alto Networks, Zscaler, and Cisco.
- Without SEO, you’re losing ground to bigger companies, even if your offering is greater.
How Buyers Look for Cyber Security SEO Solutions
- B2B Cybersecurity Buyer Journey:
Most B2B buyers in cybersecurity undergo three main stages:
Awareness:
Searches such as “What is ransomware?” and “Top cybersecurity trends 2025”
Consideration:
“Best endpoint security for SMB”; “EDR vs MDR comparison”
Choices:
“CrowdStrike pricing”, “Arctic Wolf vs SentinelOne reviews”
Real-World Illustration:
A 2023 Google B2B survey found that 89% of B2B researchers utilize the internet for research, with over 70% seeing video content before contacting a sales representative.
- Long-Tail Keywords Result in Higher Conversions.
Terms like “best XDR platform for small law firms” may have a lesser volume, but they convert 5-10 times higher than generic searches.
The Blueprint of Cyber Security SEO Strategy: The Complete Framework
Crafting an SEO strategy for a cybersecurity organization entails balancing technological precision with authoritative content and specific commercial objectives. Here’s how to accomplish it in seven thorough steps:
Summary Table: The Blueprint of Cyber Security SEO Strategy
| Strategy Phase | Key Focus Areas | Action Steps | Cybersecurity Example |
| 1. Audit & Baseline | Understand your current SEO health and visibility | – Run SEO audit (technical, on-page, off-page) – Analyze traffic & keyword benchmarks | Use Ahrefs to audit broken links on /threat-detection page |
| 2. Audience & Intent | Identify buyer personas and search intent | – Define ICPs (CISOs, IT managers, DevSecOps) – Map content to stages (awareness → decision) | Map “SIEM vs SOAR” to mid-funnel; “What is Zero Trust?” to top-funnel |
| 3. Keyword Research | Discover high-value and intent-aligned keywords | – Target technical + business terms – Use Ahrefs, SEMrush, Google Search Console | “Managed Detection and Response pricing,” “XDR for financial firms” |
| 4. Content Creation | Build authoritative, valuable, and optimized content | – Create expert-led blogs, guides, case studies – Implement E-A-T principles | Publish “Zero Trust Guide for Financial Institutions” authored by a CISO |
| 5. On-Page Optimization | Optimize each content piece for UX and SEO | – Use structured headers, keywords, schema – Optimize CTAs, load speed, and mobile-friendliness | Add FAQ schema to “Cloud Security Assessment” page |
| 6. Technical SEO | Ensure performance, indexability, and security compliance | – Improve Core Web Vitals – Secure with HTTPS, fix crawl issues | Enable HSTS, reduce unused JS on product pages |
| 7. Link Building | Increase authority through strategic backlinks | – Outreach for guest posts – Create linkable assets like reports, tools | Build links via “2025 Ransomware Threat Report” |
| 8. Measurement & ROI | Track and adjust SEO performance over time | – Monitor KPIs: rankings, traffic, conversions – Attribute leads to SEO | Use GA4 & HubSpot to track leads from “SOAR platform comparison” page |
| 9. Continuous Improvement | Evolve with updates, feedback, and market trends | – Refresh content quarterly – Follow Google algorithm and cybersecurity trends | Update “Top SIEM Tools” guide after new product releases |

Step 1: Define your business goals and target audience.
Are you looking for enterprise CISOs or small company owners?
What are your ideal customer’s pain points: ransomware, compliance, or internal threats?
Set SMART targets, such as “increase organic leads by 40% within 12 months.”
Pro tip: Align SEO objectives with marketing and sales funnels (ToFu, MoFu, BoFu).
Step 2: Competitor SEO Analysis
Utilize tools like Ahrefs and SEMrush to:
Identify who ranks for your desired keywords.
Analyze their backlink profiles and top-performing pages.
Benchmark Domain Authority and Content Depth.
Compare your website to Rapid7, Fortinet, or Sophos to identify content and backlink deficiencies.
Step 3: Perform Cybersecurity Keyword Research.
Use particular, high-intent keywords (such as “managed detection and response provider”).
Include question-based questions (e.g., “What is XDR?” or “How does threat hunting work?”).
Concentrate on long-tail variants to limit competition and increase conversions.
Tools: Google Keyword Planner, AnswerThePublic, Ahrefs, and SurferSEO.
Step 4: Create an SEO-optimized Content Strategy
Map keywords to content forms including blogs, solution pages, FAQs, and webinars.
Prioritize evergreen and authoritative guides (e.g., “Complete Guide to Zero Trust Architecture”).
Create subject clusters and internal linkages to improve the site structure.
Editorial Calendar Tip: Plan material around cybersecurity events (such as Cybersecurity Awareness Month and the RSA Conference).
Step 5: Optimize on-page elements.
Keyword-rich meta titles and descriptions, as well as engaging calls to action
Use the H1-H3 tags logically for semantic structure.
Provide internal links to related services and cornerstone material.
Add alt text to photos including encryption, threat detection, and so forth.
Step 6: Improve technical SEO
Incorporate schema markup (FAQ, product, article).
Reduce files and allow caching to improve website performance.
Ensure that all pages utilize HTTPS and canonical URLs.
Submit your XML sitemap to Google Search Console.
Step 7: Promote Content and Create Links.
Share posts on LinkedIn, Reddit’s cybersecurity forums, and Twitter/X!
Collaborate with partners on backlinks from blogs and directories.
Turn technical documents into infographics, films, or webinars.
Tip:
Share your threat research with media or speak on cybersecurity podcasts.
By following this strategy, your cyber security organization can gradually construct a dependable, high-performing SEO engine that attracts the proper visitors, fosters brand confidence, and generates qualified leads.
Keyword Research for Cyber Security SEO: Look Beyond “Antivirus”
Cybersecurity keyword research requires precision, its context, and foresight. It’s not enough to uncover high-volume phrases; you also need to understand what your target audience is looking for based on their degree of knowledge, role, and urgency.
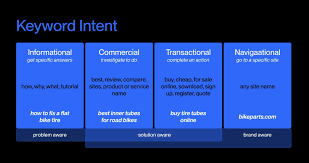
- Begin with core buckets:
Categorize your keyword list based on customer intent and product/service types:
- Threat-Based Keywords:
“Ransomware Protection Software,” “DDoS mitigation service,” “phishing detection tools”
- Solution-Based Keywords:
“SIEM Platform for Healthcare,” “cloud security posture management,” “XDR vs MDR”
- Compliance and regulations:
“HIPAA cybersecurity checklist,” “SOC 2 Type II penetration test requirements”
- Educational and awareness:
“What is zero trust security,” “How endpoint detection works,” “Cybersecurity for remote teams”
- Branded and Competitive Terms:
“CrowdStrike Alternative,” “SentinelOne vs Palo Alto Networks”
Understand the buyer’s journey.
Match keyword types with the funnel stages:
| Stage | Keyword Types | Examples |
| Top of Funnel (ToFu) | Educational, awareness, questions | “What is phishing,” “cybersecurity checklist for SMBs” |
| Middle of Funnel (MoFu) | Solution-aware, comparison | “Top endpoint protection software,” “XDR vs EDR” |
| Bottom of Funnel (BoFu) | High-intent, commercial | “Buy SIEM tool,” “best SOC as a service provider” |
Use Advanced Keyword Tools
Use these platforms to identify keyword opportunities:
Ahrefs or SEMrush: Keyword volume, difficulty, and gaps
SurferSEO: NLP-based keyword recommendations and SERP analysis.
Google Search Console: To view current keyword performance
Answer The Public: For subject inspiration and customer insights.
Exploding Topics: Emerging security trends
Identify Long Tail and Voice Search Phrases
Concentrate on intent-rich, specialized questions (FAQs). These frequently convert better and face less competition.
For example,
- “Best managed SOC provider for fintech”
- “Does HIPAA require vulnerability scanning”
- “How to create a cybersecurity policy for startups”
Analyze SERP Intent
- Before targeting a term, conduct your own search:
- Is Google delivering blog content, product sites, and comparison tables?
- Do the top results respond to “how,” “what,” or “which” questions?
- Can your material be more informative, current, or visually appealing?
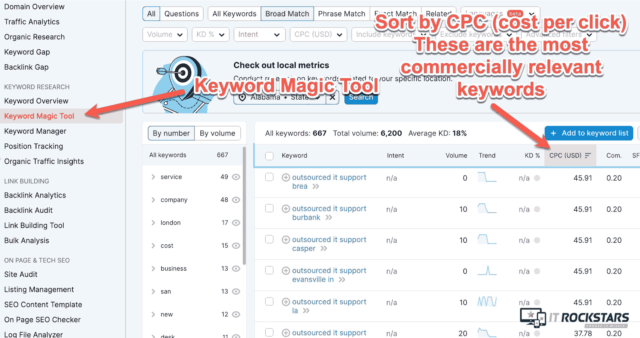
Real-World Example: Keyword Targeting for MSSPs
A controlled security service provider targeting mid-market clients may achieve high-converting results with:
- “Outsourced SOC pricing comparison”
- “24/7 MDR service for financial firms”
- “MSSP vs MSP cybersecurity”
These phrases are strongly related to bottom-funnel buyer intent and allow the building of highly targeted landing pages or sales-enablement blog material.
Takeaway:
To do effective keyword research in cybersecurity, you must combine technical knowledge with insights into search behavior. It’s not just about volume; it’s all about strategic relevance and searcher intention.
On-Page for Cyber Security SEO: Content that Converts
Cyber security audiences are technologically adept, sceptical, and time-constrained. On-page SEO must consequently strike a balance between keyword optimization, authority development, and trust. Your material must be instructional, truthful, and persuasive—while also being search engine optimized.
Summary Table: On-Page for Cyber Security SEO
| On-Page Element | Why It Matters in Cybersecurity | Best Practices / Tips |
| Page Titles & Meta Descriptions | Attracts clicks and improves CTR in SERPs | Use targeted keywords, highlight value, stay under 155 characters |
| Header Tags (H1, H2, H3) | Helps both SEO and technical readers scan easily | Organize content logically, include relevant keywords |
| SEO-Friendly URLs | Improves readability and keyword alignment | Keep URLs short, descriptive, and hyphenated |
| Content Depth & E-A-T | Builds authority and credibility for sensitive topics | Add author bios, cite industry sources (e.g., NIST, CISA) |
| Internal Linking | Boosts site navigation and distributes SEO value | Link related posts, services, case studies |
| Schema Markup | Enables enhanced SERP features | Use FAQ, Article, SoftwareApplication schemas |
| Multimedia Optimization | Improves engagement and page experience | Compress images, add keyword-rich alt text, use infographics |
| Cyber-Specific Content Formats | Matches the buyer journey with the right content types | Use guides, comparisons, how-tos, and case studies |
Key Elements for Effective On-Page Cyber Security SEO:
- Page titles and meta descriptions.
- Include the important keywords organically.
- Address the audience’s concerns or curiosities (e.g., “Prevent Ransomware Attacks | XDR Solutions for Enterprise”)
- Maintain meta descriptions under 155 characters to avoid truncation in SERPs.
- Header tags (H1, H2, and H3)
- To structure your material, use clear, keyword-rich headers.
- Improve scalability.
- Help Google grasp the topical hierarchy.
- Align with how readers absorb technical material.
- SEO-friendly URLs
- Use short, descriptive, and clear URLs.
- Example: yourdomain.com/zero-trust-architecture-guide.
- Avoid using extra arguments or unclear URLs, such as page.id=23
- Content Depth and E-A-T (Expertise, Authority, and Trustworthiness).
- Google promotes cybersecurity material created by industry pros.
- Include author biographies, references to certificates, or links to white papers.
- Cite credible sources such as NIST, CISA, OWASP, and Gartner.
- Internal Linking.
- Help users (and bots) navigate your cybersecurity ecosystem:
- Link to blog pieces, case studies, tools, or service sites.
- Helps minimize bounce rate and enhance time on site.
- Multimedia Optimization
- Use infographics, charts, and diagrams to communicate complicated topics (e.g., Zero Trust, Kill Chain).
- Make use of alt text that appropriately describes photos, including keywords where applicable.
- Compress pictures to preserve quick page performance.
Summary Table: Key Elements for Effective On-Page Cyber Security SEO
| Element | Description | Cybersecurity-Specific Tips |
| Page Titles & Meta Descriptions | First impressions in SERPs; impact CTR | Address pain points (e.g., ransomware, zero trust); stay concise & clear |
| Header Tags (H1–H3) | Structuring content for users and crawlers | Use headers to answer key security questions (e.g., “What is SASE?”) |
| SEO-Friendly URLs | Clean, keyword-rich, and readable URLs | Include product or threat terms like /xdr-guide or /malware-prevention |
| Content Depth & E-A-T | Establishes authority and credibility | Cite trusted sources (NIST, CISA, Gartner); add author bios with credentials |
| Internal Linking | Connects related content and improves crawlability | Link to related tools, services, use cases, and glossary pages |
| Schema Markup | Enhances SERP results with structured data | Use SoftwareApplication, FAQPage, and Article schema types |
| Multimedia Optimization | Boosts engagement and supports complex topic explanations | Include annotated diagrams of frameworks (e.g., MITRE ATT&CK), use alt text |
| Content Formats | Aligns with buyer journey & SEO goals | Use how-tos, case studies, whitepapers, comparisons for each funnel stage |
Effective Content Formats for Cyber Security SEO
Explainer Blogs:
“What is a Secure Access Service Edge (SASE)?”
Video Tutorials:
“How to Configure MFA for AWS Accounts”
Comparisons, including “CrowdStrike vs SentinelOne:
Which EDR Tool Wins?”
Whitepapers and Guides:
Downloadable materials that serve as lead magnets.
Case Studies:
Display genuine outcomes from your equipment or services.
Real-World Illustration: On-Page Cyber Security SEO That Converts
Rapid7 organizes its product and resource sites using:
- Scannable headers.
- Integrated demo CTAs.
- Integrated videos and diagrams
- Internal links for webinars, documentation, and blogs
As a consequence, they score highly for mid- and bottom-funnel phrases such as “vulnerability management platform” and “SIEM for cloud environments.”
Takeaway: On-page Cyber Security SEO is more than simply appeasing algorithms; it’s about building trust. Your page should seem as though like it was created by and for professionals.
Technical SEO: Security and Site Performance
In cybersecurity, trust is essential and technical SEO is your digital handshake. It guarantees that your site not only ranks high, but also loads quickly, is safe, and communicates professionalism to both search engines and users.
Technical SEO is the process of enhancing your website’s infrastructure so that search engines can efficiently crawl and index it. This is especially important for cybersecurity websites, since your audience demands impenetrable security, smooth performance, and zero tolerance for poor digital hygiene.
Key Areas of Technical SEO for Cyber security Businesses
- HTTPS and site security
They are essential for reputation in the cybersecurity industry.
Check that your SSL certificate is genuine and that it is being used throughout your website.
Google may penalize or warn non-HTTPS sites, particularly in critical sectors such as cybersecurity.
Pro Tip: Use free tools like SSL Labs to check the strength of your certificates and detect weaknesses.
- Page Speed Optimization
Google utilizes site speed as a ranking factor.
Cybersecurity purchasers will not tolerate a sluggish website, especially if they are browsing during an incident or procurement window.
Key actions:
- Compress and lazy-load pictures.
- Minimize JavaScript and CSS files.
- Use browser caching and a content delivery network (CDN).
- Use Google PageSpeed Insights or GTmetrix to track load times and obtain practical recommendations.
- Mobile responsiveness.
Mobile devices account for more than fifty percent of all worldwide online traffic. Even B2B cybersecurity execs use their phones and tablets when traveling or after hours.
Make sure your site has a flexible layout and passes Google’s Mobile-Friendly Test.
- XML Sitemap and Robots.txt Optimization
These files specify which pages search engines should crawl and index.
Submit a sitemap to Google Search Console and Bing Webmaster Tools.
Use Robots.txt to prevent admin or duplicate pages from being crawled (for example, login portals or test environments).
Cyber Tip: Don’t mistakenly block crucial folders like /blog/ or /solutions/ in your robots.txt file; this happens more frequently than you realize.
- Structured data (schema markup).
Structured data helps search engines comprehend your website’s content, resulting in rich SERP results.
Relevant schemas for cyber security SEO sites:
- SoftwareApplication
- Organization
- FAQPage
- BreadcrumbList
- Event (for webinars and virtual demonstrations)
Use Google’s Rich Results Test to check your schema.
- Core Web Vitals (UX Signals).
Google’s ranking system includes several measures, which represent real-world user experience:
- LCP (Largest Contentful Paint) – Speed of loading
- FID (First Input Delay) – the pace of interaction
- CLS (Cumulative Layout Shift) provides visual stability.
To maximize these:
- Defer non-critical scripts.
- Preload fonts.
- CSS confinement is useful for ensuring layout stability.
Google Search Console allows you to track core web vitals.
- Canonicalization and Duplicate Content Control
Cyber security companies frequently publish whitepapers, product briefings, and partner information across many domains, resulting in duplicate content issues.
Best practices:
Use canonical tags to refer to the original version.
Avoid thin or redundant service pages (for example, “Managed SOC” versus “SOC-as-a-Service”).
Combine comparable materials to create complete pillar pages.
- Error Resolution and Crawl Health.
Common concerns are:
- Broken internal connections
- 404 pages due to obsolete blog links.
- Redirect chains: 301 > 302 > destination.
Use tools like Screaming Frog SEO Spider or Ahrefs Site Audit to detect these issues early.
Summary Table: Technical SEO for Cyber Security
| Technical SEO Element | Why It Matters in Cybersecurity | Key Tools / Actions |
| HTTPS & SSL | Builds user trust and meets Google’s security standards | SSL Labs, Qualys, Search Console |
| Page Speed Optimization | Faster access during urgent research or incidents | GTmetrix, PageSpeed Insights, Cloudflare CDN |
| Mobile Responsiveness | Ensures visibility across devices | Google Mobile-Friendly Test |
| Sitemap & Robots.txt | Directs search engine crawling behavior | GSC, Yoast SEO, Screaming Frog |
| Structured Data / Schema | Enables rich search results for better visibility | Schema.org, Rich Results Test |
| Core Web Vitals | Measures user experience on real devices | Search Console, Lighthouse, Chrome UX Report |
| Canonicalization | Prevents duplicate content dilution | Yoast, Ahrefs, Screaming Frog |
| Crawl Health & Errors | Maintains indexability and UX | Screaming Frog, Ahrefs, Sitebulb |
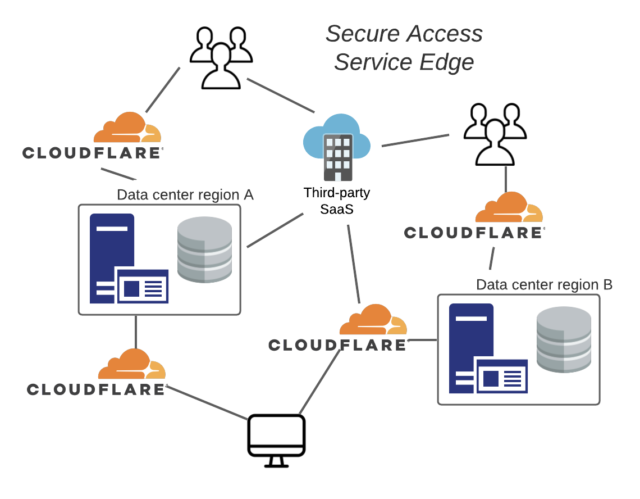
Real-World Example: Cloudflare’s flawless technical SEO.
Cloudflare, a large cybersecurity infrastructure company, specializes in technical SEO. Their website:
- Loads in under one second worldwide (via their own CDN edge nodes).
- Has proper HTTPS setup and supports HTTP/2.
- Structured data is commonly used in blogs, products, and job ads.
- Maintains a clean robots.txt and sitemap.xml.
As a result, they dominate SERPs for highly competitive phrases such as “WAF service” and “DDoS protection,” and their sites are swiftly indexed due to optimized crawl patterns.
Key Takeaway:
Technical SEO is essential for cybersecurity businesses. It demonstrates your competency, integrity, and attention to detail. A safe, quick, and well-structured website is not just helpful for rankings; it also communicates to your viewers the way you practice what you teach.
Off-Page SEO and Link Building for the Cyber Security SEO Niche
When it comes to cybersecurity, authority and credibility are essential not just in your goods, but also in your online presence. Off-page SEO is the process of establishing online credibility through the acquisition of high-quality backlinks, mentions, and exposure on third-party sites.
Consider backlinks to be positive endorsements from other websites. Backlinks from credible sources like as Gartner, TechCrunch, ZDNet, or.edu/.gov domains may significantly improve cybersecurity businesses’ rankings and trustworthiness.
Summary Table: Off-Page Cyber Security SEO
| Element | Description | Cybersecurity-Specific Application |
| Backlink Quality over Quantity | Focus on backlinks from trusted, authoritative domains | Aim for links from CISA, NIST, tech blogs, cybersecurity journals |
| Guest Posting | Contribute expert articles to relevant blogs or media sites | Write for ThreatPost, Dark Reading, Hacker News, Security Boulevard |
| Digital PR & Thought Leadership | Gain mentions via expert quotes, research, or newsjacking | Pitch insights during major breaches or compliance changes (e.g., NIS2) |
| Data-Driven Assets | Create original reports, surveys, tools, or benchmarks | Example: “Annual Ransomware Readiness Survey” |
| Broken Link Building | Find dead links on cybersecurity sites and offer your resource instead | Replace outdated “OWASP 2016” links with your updated threat guide |
| Partnership Content | Collaborate with vendors, MSSPs, or SaaS providers | Co-author a whitepaper with a cloud security vendor |
| Community & Forum Engagement | Provide value in Reddit, GitHub, Spiceworks, and Stack Overflow discussions | Share relevant tools or guides when answering security questions |
| Social Signals | Improve visibility through LinkedIn, X (Twitter), YouTube, etc. | Promote content via infosec hashtags, cybersecurity influencers |
| Local & Niche Directories | Submit to cybersecurity-specific and local business directories | Example: UpCity, Clutch, Cybersecurity Ventures directory |
Effective Link Building Strategies for Cyber Security Firms:
- Digital PR Campaigns.
Submit original cybersecurity research, threat reports, or insights to news organizations and security magazines.
For example, Wired, Forbes, and CSO Online frequently link to Bitdefender’s Threat Debriefs.
Contribute expert quotations using sites such as HARO, Qwoted, or Help a B2B Writer.
- Guest posting on technology and security blogs.
Reach out to credible websites and offer to provide material on specialist themes such as:
“Securing Kubernetes at Scale”
“XDR vs. EDR: What CISOs Need to Know”
Target sites with DA 50 or above and overlapping audiences (for example, DarkReading and DevSecOps.org).
- Resource Link Building
Develop high-value assets such as:
- Cybersecurity glossaries
- Compliance checklists (for example, SOC 2, HIPAA)
- Toolkits and comparison matrices
- Share these materials with colleges, SaaS partners, and security groups.
- Thought Leadership for LinkedIn and Twitter
Distribute blog postings, whitepapers, and threat studies via social media.
Tag influencers and corporations.
Engage in discussions on infosec trends or CVEs.
Backlinks are frequently obtained indirectly via sharing and reusing content.
- Partner and Vendor Link Exchanges
Collaborate with:
- MSPs and MSSPs
- Security Training Providers
- SIEM, SOAR, and endpoint providers
Provide cross-links between integration guidelines, case studies, and partner pages.
- Sponsor and speak at cybersecurity events.
Industry conferences frequently include links to the speaker’s corporate websites.
Black Hat, DEF CON, RSA, and BSides are high-authority domains.
Submit speaking abstracts and add a link to your firm in the bio.
Effective Link Building Strategies
| Tactic | Example | Link Opportunity |
| Publish a Threat Intelligence Report | “2025 Ransomware Trends” | Media, analyst, and .gov links |
| Develop Free Tools or Calculators | “Phishing Simulation ROI Calculator” | Developer blogs, GitHub, Reddit |
| Create Visual Assets | Infographics on Zero Trust, MITRE ATT&CK | Security publications, SlideShare embeds |
| Host Webinars | “How to Prepare for a SOC 2 Audit” | Event listings, partner promotions |
| List Integrations | “Integrates with Okta, AWS GuardDuty” | Backlinks from partner product pages |
Real-World Illustration: CrowdStrike’s Link Strategy.
CrowdStrike creates effective off-page SEO by:
Publishing timely threat research, such as Falcon Overwatch.
Speaking at business events and backlinking speaker profiles.
Collaboration with AWS, Azure, and Google Cloud for co-branded sites.
CrowdStrike’s activities enable them create thousands of backlinks from high-authority domains, which boosts their ranking power for phrases like “endpoint protection platform” and “managed threat hunting.”
Key Takeaway:
Off-page SEO isn’t about spamming link building or purchasing backlinks; it’s about establishing your position in the cybersecurity discourse. When your brand is seen as a reliable source of knowledge and ideas, other websites will automatically connect to you—and search engines will reward that authority.
Backlink Outreach Checklist for Cyber Security SEO
Use this checklist to launch a successful and ethical link-building campaign for cybersecurity content.
The preparation phase
Identify your backlink goals, such as domain authority, traffic, and specialty relevance.
Audit the existing backlink profile (using Ahrefs, SEMrush, or Moz).
Find 20-50 cybersecurity-related websites, blogs, and news outlets.
Create or identify a linkable asset (guide, report, tool, etc.).
Check website quality: DA 40+, HTTPS, active blog, non-spammy.
Outreach Setup
Create a contact list: name, role, email, website, and LinkedIn.
Prospects can be divided into segments, such as journalists, bloggers, merchants, and educators.
The execution phase
Send 5-10 outreach emails every day to circumvent spam filters.
Monitor opens, clicks, and answers.
Respond within 24 hours to all responses.
Make useful enhancements (e.g., media kits, co-branding choices).
Post outreach
Use Ahrefs or Google Search Console to track earned backlinks.
Thank connections and develop long-term ties.
Update material frequently to keep backlinks fresh.
Repurpose successful material for broader exposure (for example, turning a blog into an infographic)
Sample Outreach Email Templates for Cyber Security SEO Backlinking



Frequently Asked Questions (FAQs) on Cyber Security SEO
- How can cyber security websites achieve SEO without sacrificing security?
To balance SEO with security:
- Use HTTPS with a good SSL certificate.
- Avoid exposing sensitive folders in robots.txt.
- To avoid SEO-related breaches, keep your CMS, plugins, and servers up to date.
- Reduce the number of third-party scripts that might lead to security issues.
- Use secure redirects (301s) correctly to maintain link equity and trust.
Pro Tip:
Use tools like SecurityHeaders.com and Google Search Console to track SEO health and security hygiene.
- How does technical SEO affect cyber security sites?
Technical SEO guarantees that your website is
Crawlable: Search engines follow proper XML sitemaps, robots.txt, and internal linkages.
Fast and responsive: Core Web Vitals (LCP, FID, and CLS) impact both SEO and user experience.
Secure: HTTPS and suitable headers (HSTS, X-Content-Type) help to convey confidence.
Mobile-friendly: Many decision-makers conduct their first research on mobile devices.
A misconfigured WAF (Web Application Firewall) or CDN (such as Cloudflare) might mistakenly block Googlebot, reducing ranks. Regular audits are needed.
- Can content marketing help cyber security firms improve their SEO?
Absolutely. Content marketing helps:
- Helpful blogs, how-to, and whitepapers can help you attract visitors with high intent.
- Develop thematic authority with long-form technical content.
- If your material is credible and referenced, it will organically generate backlinks.
- Educate your target audience and guide them through the funnel.
For instance,
A blog titled “What Is SOAR and Why It Matters in 2025” might rank for long-tail keywords and direct visitors to your product demo page.
- How can backlinks help cyber security firms enhance their SEO?
Backlinks serve as votes of confidence from other sites.
Regarding cyber security:
Backlinks from authoritative websites (such as NIST, TechCrunch, and OWASP) increase credibility.
They pass Domain Authority (DA), which helps you rank for competitive phrases.
High-quality backlinks speed up the indexing process and make your content look more trustworthy.
Tools like as Ahrefs, SEMrush, and HARO can assist you.
- What sorts of content should cybersecurity businesses prioritize for SEO?
- The best-performing forms include:
- Explainer articles (for example, “What is XDR?”)
- Comparative pieces (e.g., “SentinelOne vs CrowdStrike”)
- Technical how-to (such as “How to Implement Zero Trust”)
Case Studies
Regulatory and compliance guidance (such as “Navigating NIS2 or GDPR”)
- How long does SEO take to provide results in the cybersecurity space?
SEO is a lengthy game. Most businesses achieve demonstrable outcomes after 4 to 6 months of sustained work. Highly competitive keywords may take longer.
Content refreshes, technological updates, and long-tail keyword targeting can all help you obtain quick results.
- Does SEO create genuine leads for cybersecurity products?
Yes. By connecting SEO with user intent and phases of the customer journey:
TOFU (top-of-funnel) material promotes awareness.
MOFU (middle-of-funnel) guides and comparisons drive engagement.
BOFU (bottom-of-funnel) pages convert leads via CTAs, demonstrations, and forms.
For example,
A well-optimized website for the “MDR pricing calculator” can generate demo requests from organic visitors.
- Do cybersecurity businesses require local SEO?
Yes, if you service certain areas (for example, SOCs, MSSPs, or IT consultancies).
Google Business Profile, location-based sites (e.g., “Pen Testing Services in NYC”), and local backlinks will assist you appear in local search results and maps.
Conclusion: SEO is a Strategic Security Asset
Cybersecurity firms can no longer afford to ignore SEO in a digital environment that is crowded with suppliers, risks, and noise. SEO makes sure that your knowledge is visible, whether you’re publishing vulnerability research, selling threat detection platforms, or providing managed security services.
This is what we have discovered:
- SEO is strategic exposure, not simply marketing. It puts your company in front of decision-makers, IT managers, security architects, and CISOs at the precise moment they are looking for answers.
- Authority-building, content relevancy, technological integrity, and keyword research all work together. Your SEO should appeal to the discerning cybersecurity buyer’s professional scepticism as well as their search purpose.
- The SEO success stories in cybersecurity, and they all adhere to the same formula: solid technological underpinnings, excellent content, reputable backlinks, and data-driven iteration.
When done correctly, SEO may increase your website’s lead generating capabilities, reduce your customer acquisition cost (CAC), and develop long-term brand equity.
Final Thought
SEO needs constant testing, monitoring, and enhancement, much like fixing software flaws. It’s a constant benefit rather than a temporary solution.
Next Steps
- Use cybersecurity-specific technologies to perform an SEO assessment.
- Create a content calendar using low-competition, high-intent keywords.
- Get useful backlinks by using our checklist and backlink outreach templates.
- Every month, track your traffic, rankings, and conversions, then make any adjustments.



